Secure Your MCP Connections
From SaaS and web chatbots to local desktop agents and MCPs, Lasso enables enterprises to confidently utilize AI across every department while keeping sensitive data and brand standards fully protected.











%201.avif)

.avif)











%201.avif)

.avif)
Why MCP Security Matters to Enterprises
Shadow MCP Sprawl
Developers install MCP servers without security review. Each connection expands your attack surface with tools that access databases, APIs, and file systems. Visibility is the first step to governance.
Prompt Injection & Tool Poisoning
MCP servers can contain hidden instructions in tool descriptions, malicious responses, and more. Attackers manipulate agent behavior through compromised servers, bypassing traditional security controls that weren't built for AI.
Evolving Compliance Standards
AI legislation is evolving fast. NIST AI RMF, EU AI Act, and industry regulations now require governance over AI agent connections. Managing these requirements without MCP security creates compliance gaps.
Accelerate the Adoption of AI Agents

Unlock the Full Potential of MCP, Trust Your Security to Scale
Comprehensive Discovery, Zero Blind Spots
Discover, inventory, and assess every MCP server across your enterprise. Get a risk score for each MCP according to its permissions, actions, description, and more. If an MCP server triggers a high risk score, manage or block it instantly.
Security Without Slowing Down
Monitor every MCP tool call in real-time to identify indirect prompt injection, memory poisoning, and other AI threats or attack techniques.
Governance Across the Execution Path
Deploy intent-aware policies in minutes to enforce role-based permissions and strict Data Loss Prevention. Lasso applies runtime enforcement to identify intent misalignment with the organization’s policies.
Automated Compliance & Usage Reports
Map your MCP policies to NIST, OWASP, MITRE and more using plug-and-play templates. Generate audit-ready reports that prove governance by analyzing MCP usage trends and flagging high-risk connections.
Core Components of MCP Security
MCP Server Discovery
Automatically discover all MCP servers connected across your organization. Inventory Claude Code and Desktop, Cursor, Windsurf, and custom agent connections. Get risk scores that highlight which servers require immediate attention.
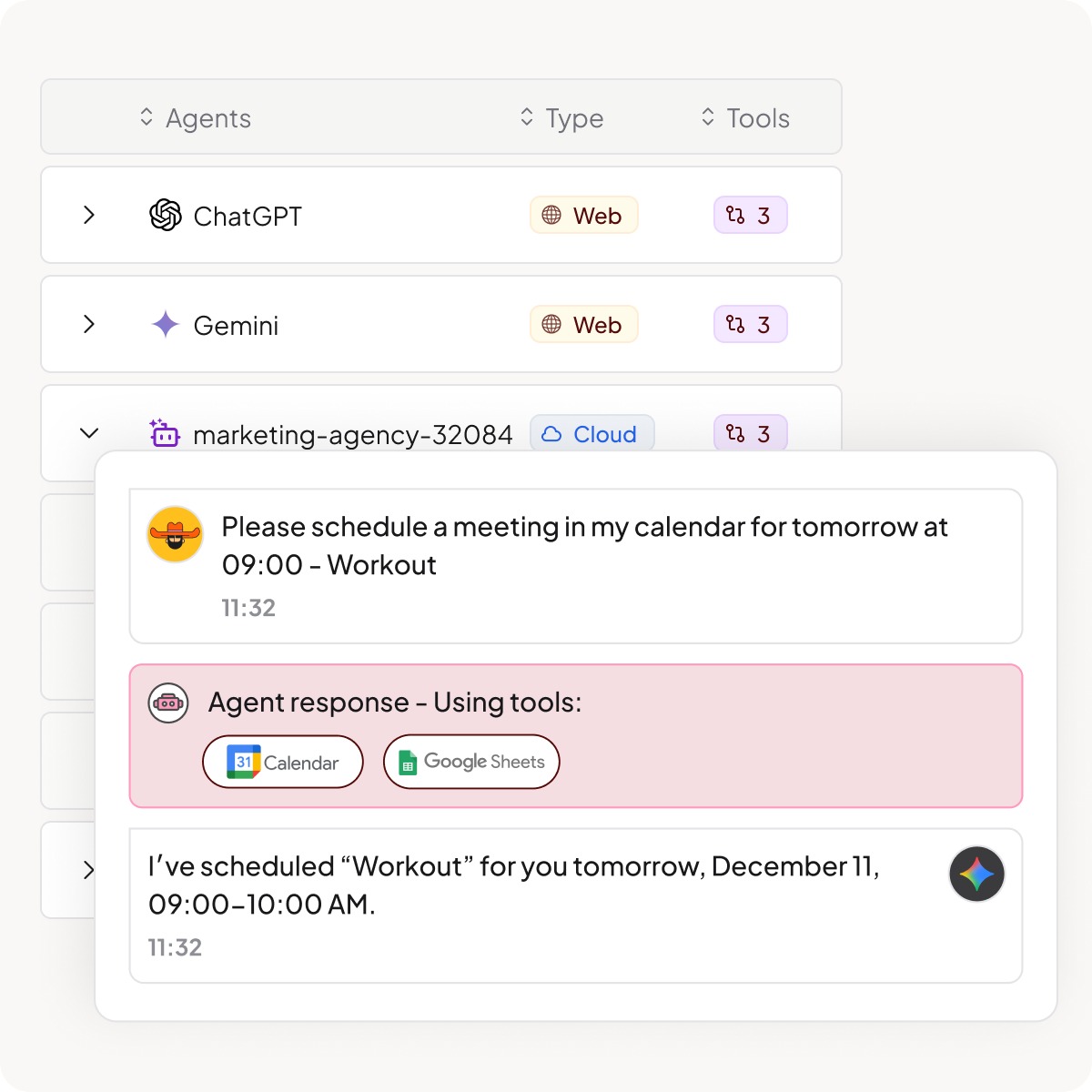
Data Loss Prevention
Detect and monitor in real-time if PII, API keys, credentials, or any other sensitive data is shared through MCP tool calls. Mask sensitive contents before they reach external servers.

Access Management & Permissions
Control which users and teams can connect to which MCP servers. Enforce role-based permissions that allow approved use cases while blocking unauthorized connections.

Audit Trails
Maintain complete audit trails of every MCP connection and tool call. Export logs to your SIEM. Generate compliance reports that prove governance over AI agent activity.

AI Threat Detection and Response
Scan MCP server tool descriptions for hidden instructions. Detect and block prompt injection attempts at the connection layer. Stop attackers from manipulating agent behavior through compromised servers.

FAQs
What is MCP security?
MCP security is the practice of protecting Model Context Protocol connections between AI agents and external tools.
- Visibility into all MCP connections across Claude Code and Desktop, Cursor, and Windsurf
- Real-time threat detection for prompt injection and data exfiltration
- Policy enforcement and access control for MCP servers
- Audit trails and compliance reporting for AI governance
Is MCP secure by default?
No. MCP has no built-in security controls. The protocol was designed for functionality, not security.
- No authentication or access control mechanisms
- No monitoring or audit trail capabilities
- No protection against prompt injection attacks
- Any MCP server can access resources without restrictions
How to secure MCP servers?
Securing MCP servers requires visibility, threat detection, and policy enforcement at the connection layer.
- Deploy Lasso MCP Gateway to monitor all connections
- Scan MCP server tool descriptions for hidden instructions
- Implement request/response filtering for all tool calls
- Enforce policies for data access and tool permissions
- Maintain audit trails for compliance and incident response
What is the difference between MCP security and API security?
MCP security differs from traditional API security because AI agents make autonomous decisions about tool usage.
- API security: Predictable request patterns, static authentication
- MCP security: Dynamic tool calls, AI-driven decisions, context-aware threats
- MCP requires prompt injection detection that API gateways don't provide
- AI agents chain multiple tool calls, creating complex attack surfaces
How do I secure Claude Code or Desktop and Cursor IDE?
Claude Code and Cursor IDE use MCP to connect AI to external tools. Lasso secures them without slowing developers down.
- Route all MCP connections through Lasso Gateway
- Discover and inventory all MCP servers connected by developers
- Block untrusted or unapproved MCP servers automatically
- Monitor tool calls for suspicious patterns and data access
What are MCP security best practices?
Follow these best practices to protect your AI infrastructure from MCP-related threats.
- Inventory all MCP servers and connections across your organization
- Implement centralized security policies and access controls
- Deploy real-time monitoring for prompt injection and data exfiltration
- Maintain complete audit trails of all AI tool interactions
- Regularly scan MCP servers for vulnerabilities and misconfigurations
How does Lasso protect against MCP prompt injection?
Lasso uses multiple detection layers to catch prompt injection attempts in MCP connections.
- Tool description scanning detects hidden instructions before server loads
- Request/response filtering analyzes every tool call for injection patterns
- Behavioral analysis flags unusual tool call sequences
- Configurable actions: block, alert, or sanitize based on your policies
What compliance standards does Lasso MCP security support?
Lasso provides audit trails and controls for major compliance frameworks.
- NIST AI Risk Management Framework
- SOC 2 Type 2, ISO 27001, ISO 42001
- EU AI Act requirements
- Industry-specific: HIPAA, PCI-DSS, FedRAMP
Does Lasso secure both Claude Desktop and Claude Code?
Yes. Lasso provides MCP security for all Claude tools that use the Model Context Protocol, not just one.
- Claude Desktop: Secure MCP connections from the Claude desktop application
- Claude Code: Monitor and protect MCP tool calls from the CLI coding assistant
- Both tools connect to MCP servers that can access files, databases, and APIs
- Lasso applies the same threat detection and policy enforcement across all Claude MCP clients
Keep up with Lasso

.png)

