How enterprises can gain visibility into AI agent usage and make informed governance decisions
A Glimpse into the Agentic Future
OpenClaw, the open-source agentic AI assistant that surpassed 155K GitHub stars within days, offers a glimpse into what the agentic AI future looks like and that future is arriving faster than most enterprises expected.
What makes OpenClaw notable among agentic tools is its scope.
OpenClaw operates as an almost autonomous agent, running locally with full system access and integrating with numerous services across messaging, productivity, browsers, and smart devices.
It can execute real-world tasks like managing emails, adjusting your smart devices based on your calendar, monitor GitHub repos and flag issues that need attention or automate workflows that span multiple apps.
For enterprises exploring the agentic workforce, this is an early preview of AI employees working alongside humans.
The productivity potential is genuine. But OpenClaw shares the vulnerabilities inherent to agentic systems, and extends them. Its broad integration surface means more credentials, more access points, more autonomous actions across services.
Add the ability to communicate with other agents (including unverified ones via platforms such as Moltbook) and the attack surface expands even further. For security teams, this is shadow AI with a broader blast radius.
Shadow AI: The Scale of the Challenge
The popularity of OpenClaw on GitHub signals broader adoption patterns. Research shows widespread unauthorized AI usage in enterprises: According to IBM & Censuswide study (11/2025), 80% of surveyed employees at organizations with 500+ employees use AI tools not sanctioned by their employer.
The combination of rapid adoption and expanded access makes agentic tools uniquely challenging to govern.
The risks here are not new, but tools like OpenClaw amplify these concerns. A misconfigured OpenClaw instance potentially exposes everything accessible from the user's machine: local files, stored credentials, connected services, and can execute unauthorized commands across all of them. The vulnerabilities are familiar; the blast radius is not.
Discovery First, Then Governance
Most coverage of OpenClaw has been alarmist. While security concerns are legitimate, the fear-based approach misses something important: employees adopt these tools because they genuinely help them work better. Blocking or ignoring the phenomenon simply shifts it beyond security's line of sight.
A more productive approach starts with discovery. You cannot govern what you cannot see. Understanding when and how tools like OpenClaw are used allows security teams to quantify actual risk, inform policy decisions, and enable controlled adoption where appropriate.
From there, it becomes a matter of risk readiness. With visibility established, security teams can make informed decisions: which tools to sanction, which configurations to allow, what guardrails to enforce. The goal isn't to eliminate AI usage, it's to bring it within a governance framework that aligns with the organization's risk tolerance.
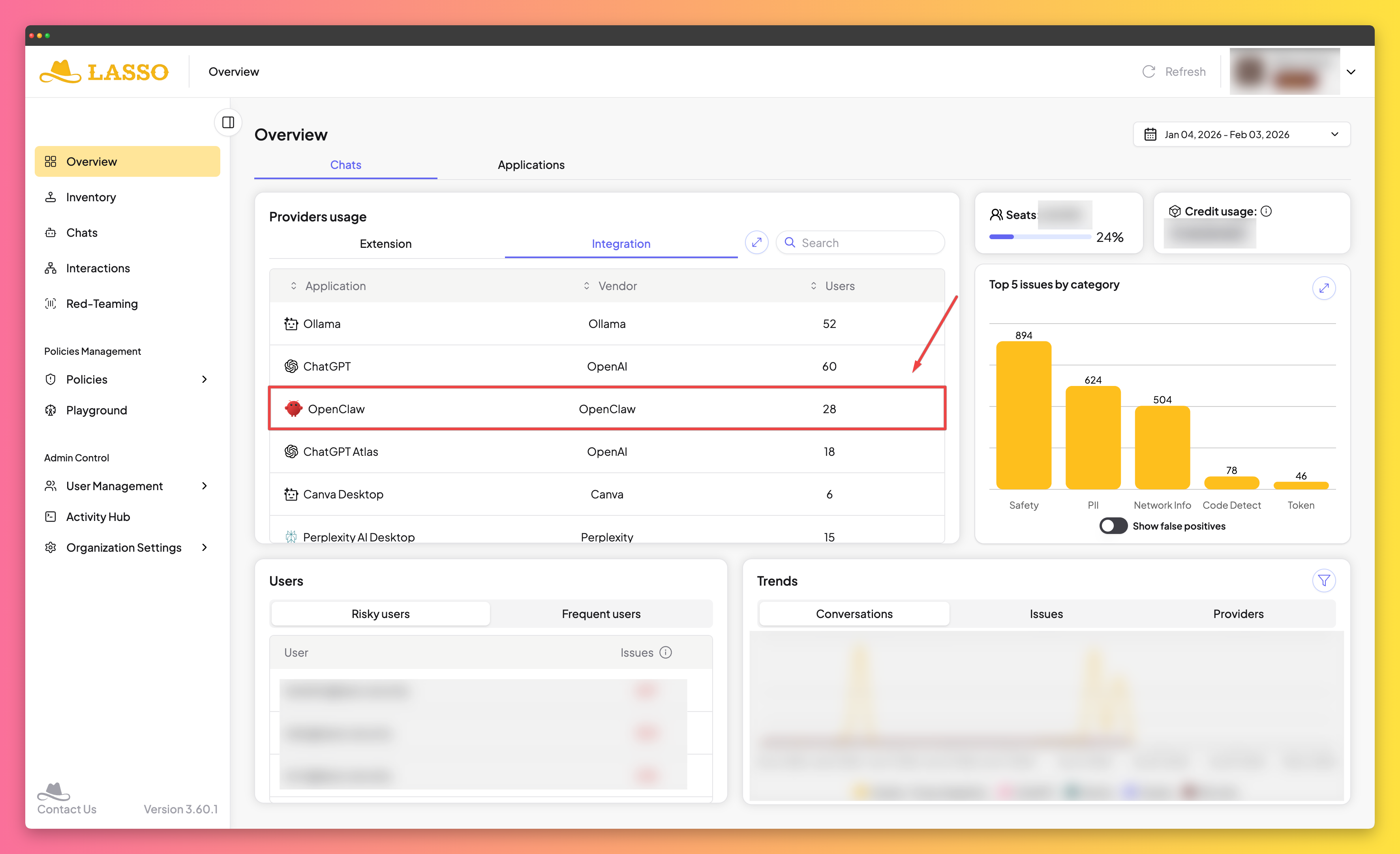
OpenClaw Discovery in Practice
OpenClaw leaves distinctive footprints across filesystem, network, and process layers. Detection can be approached in two ways:
- One-time scan: Comprehensive check of all indicators.
- Continuous monitoring: Real-time alerts when processes launch, ports open, or relevant files change.
Endpoint artifacts can be detected through scans by endpoint security tools. Below are examples of filesystem indicators that signal OpenClaw installation and usage:
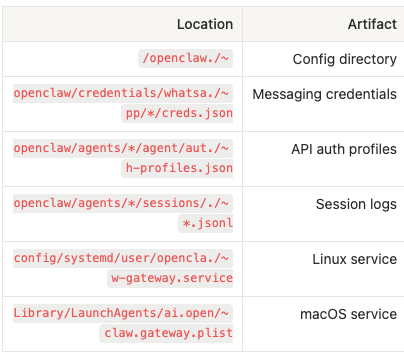
Local Gateway Ports (Real-Time Detection)
OpenClaw operates through local network services:
- TCP 18789: WebSocket Gateway (primary command channel)
- TCP 18793: Canvas Server (visual interface)
An open port 18789 indicates an active, operational agent. Monitoring these ports provides real-time visibility into when employees are using the tool.
Process Monitoring
OpenClaw creates identifiable processes, and processes with OpenClaw in the path. Process monitoring enables real-time alerting when the tool launches.
Limitations of Network Traffic Analysis
Monitoring connections to AI APIs or messaging platforms seems intuitive but has limitations.
A connection to web.whatsapp.com could be normal browser usage; a call to Anthropic API or OpenAI API could originate from any approved application or developer workflow.
Traffic patterns between AI agents and legitimate tool usage are difficult to distinguish. Endpoint-based detection avoids this ambiguity.
Managing Residual Risk
Agentic AI introduces risks that technical controls cannot fully eliminate. LLM-powered agents behave non-deterministically. Data flows through external providers.Frameworks like Meta's "Agents Rule of Two" offer useful guidance here.
Inspired by Chromium's security policy of the same name and Simon Willison's "Lethal Trifecta", the principle identifies three factors that compound agent risk: access to untrusted data, access to private data, and the ability to communicate externally.
When all three are present, exposure increases significantly. Constraining any one of these dimensions can meaningfully reduce risk, though each involves tradeoffs in capability or user friction.
Agentic risks cannot be eliminated, but they can be managed through thoughtful design constraints and clear organizational risk tolerance. Discovery is the first step; governance decisions follow from there.
Preparing for the Agentic Workforce
OpenClaw represents an early wave of autonomous AI agents that will increasingly appear in enterprise environments. The productivity potential is genuine, but so are the risks.
Tools like OpenClaw extend the vulnerabilities inherent to AI systems: more integrations, more credentials, more autonomous actions, and a broader attack surface.
For security teams, this is shadow AI at a new scale.The path forward is not prohibition. It is informed governance built on visibility.
Discovery provides the foundation for understanding what tools are in use, how they are configured, and what access they have.
From there, organizations can assess real risk and make deliberate decisions about enablement and restriction.
The agentic workforce is arriving. With the right tools and controls, enterprises can shape how it enters their environment rather than react after the fact.